Strategy Day
& RISK MANAGEMENT
Cybersecurity

26 MARCH 2025
/
Zurich
/
11 Speakers
/
Networking
> SECURE YOUR TICKETS!
Networking, Exchange and Strategic Update for Cybersecurity and Risk Professionals
Cybersecurity is a never-ending war game. GenAI and Quantum Computing change the game. 5G, Web3, IoT, remote work and a vastly scaling cloud infrastructure cause a further increase of touchpoints, data, speed, applications and complexity. Attackers truly have a new set of opportunities, and so do defenders. On top of the tech challenges military and economic conflicts cause a more heterogenous and capable spectrum of threats – urging security professionals to tackle powerful state players, organized crime and untrustworthy companies even more.
At Cybersecurity Strategy Day CISOs meet to exchange perspectives, experiences and views on the current challenges and solutions.
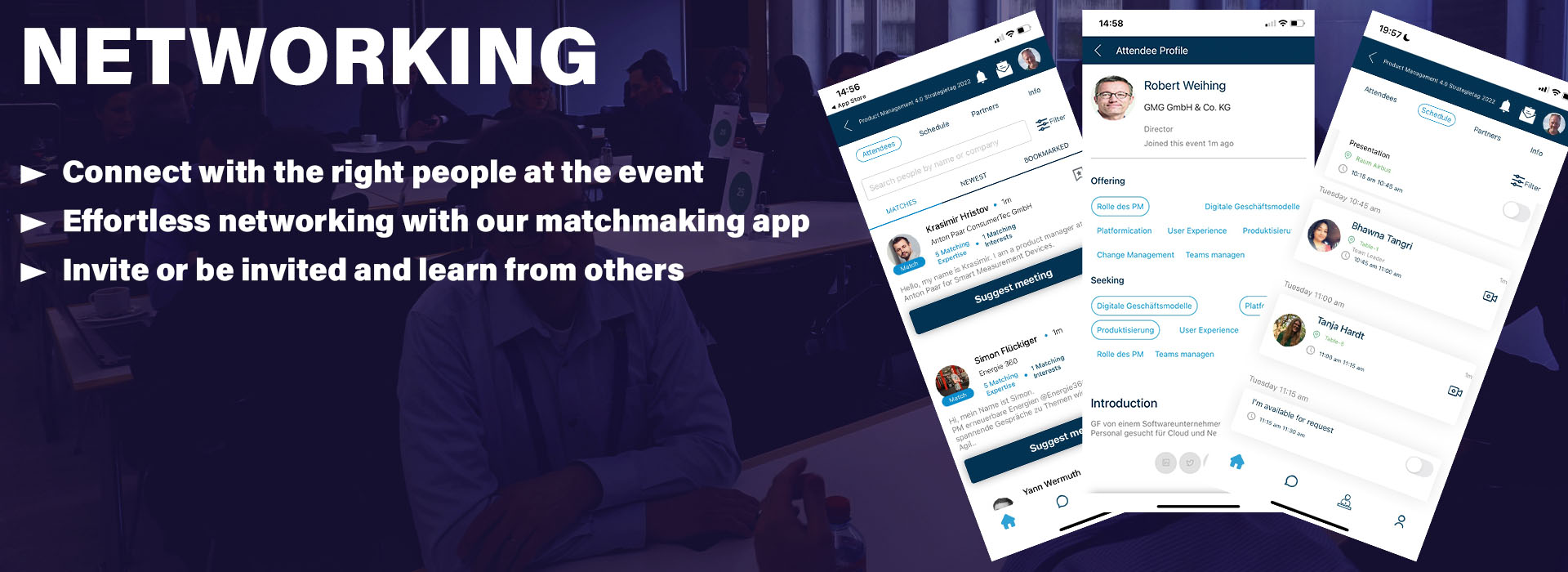
Read MoreLots of time and space for networking
- Best practices: Selected business cases and inspiring talks
- Matchmaking: Interests and competencies of all attendees
- Networking: Matched and pre-arranged one on one meetings
- Access to Networking app “Cintona”
- Possibility to join online via livestream
- Access to slides and video recordings of the sessions
Topics (Selection)
- Current Strategic Threats
- Strategic Models
- Cybersecurity Management Models
- NIS-2
- MDR (Managed Detection and Response)
- Realistic and feasible ways to create more awareness and skills
- E-Learning and Gamification to build skills
- XDR (Extended Detection and Response)
- SIEM (Security Information and Event Management)
- SOAR (Security Orchestration, Automation and Response)
Subscribe for updates
Speaker
Romano Ramanti, Zürcher Kantonalbank
Certified Ethical HackerAlexander Sagawe, UBS
Director Global OperationsPietro Vassalli, Gruppo Sicurezza SA
Cyber Security ManagerAndra-Irina Vasile, SIX
Senior Cyber Defense Strategy and Advisory SpecialistJakub Bryl, Tenthpin
Global Head of Security and Compliance (CISO)Mirko Helbling, RUAG
Director of Cyber SecurityCornelia Puhze, Switch
Security Awareness ExpertMarcelo Sousa Ancelmo, KPMG Switzerland
Head of Solution Architecture
26. März 2025
10:30 - 11:15
Coffee break & Networking talks
12:30 - 13:30
Lunch break
14:30 - 15:00
COFFEE BREAK & NETWORKING TALKS
Location